TCP / IP
There are various protocols for Internet programs to communicate with, such as HTTP, SFTP and FTP. The most common protocol used in Internet protocols, as you all know, is IP, and the important thing here is that TCP/IP is not a hierarchy, but a protocol.TCP/IP runs on top of TCP/IP structural hierarchy slightly different from OSI7 hierarchy.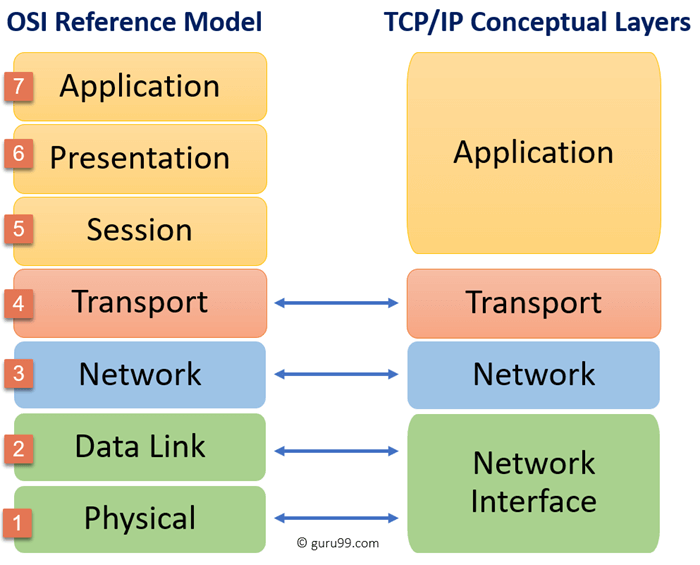
It looks a little different from the OSI7 hierarchy.
You can see that the number of tiers is different, OSI is seven, while the TCP/IP tier is all four.
1. Network Interface Layer
This tier is responsible for reliable data transmission between Node and Node.
The network interface hierarchy is responsible for the physical and data link tiers of the OSI7 hierarchy.
Therefore, MAC addresses are used in this hierarchy.
MAC addresses are used because the network interface hierarchy covers the data link hierarchy.
The equipment above is a LAN card. The exact name is NIC and Network Interface Card.
Network communication is not possible without a LAN card. A device that operates in the network interface hierarchy.
LAN includes Ethernet, TokenRing, FDDI, X.25, FrameRelay, PPP, and so on.
2. Internet Layer
The network hierarchy of the OSI7 hierarchy. You will be responsible for routing between hosts, such as the OSI7 hierarchy.
The protocols that work in the Internet hierarchy are:
IP (Internet Protocol) : Untrusted, unconjugated Datagram Protocol
Address Resolution Protocol (ARP) : Address translation protocol. Protocol that converts IP addresses to MAC addresses
RARP (Reverse ARP) : a protocol that looks for an IP address by MAC address.
ICMP (Internet Control Message Protocol) : State Diagnostic Message Protocol, which is used by leading programs to ping
Internet Group Message Protocol (IGMP) : protocol for multicast
3. Transport Layer
Same as the transmission hierarchy in OSI7 hierarchy. A hierarchy responsible for reliable data transmission between processes.
A logical address is required to be responsible for process-to-process forwarding, but the port number used by the process is used as its logical address.
The protocols that work in the transport hierarchy are:
TCP (Transmission Control Protocol) : A reliable connection-oriented protocol that provides error recovery through error handling and retransmission of the packets. Therefore, there is a lot of information attached to the TCP header.
User Datagram Protocol (UDP) : Untrusted and unreliable protocol. Do not take action if you lose your packet or if there is an error. Therefore, UDP headers have a simple structure.
4 . Application Layer
The tier closest to the user. It is responsible for everything from 5 to 7 OSI tiers.
Server and client applications operate in this hierarchy. Services such as browsers and telnet that we know work in this hierarchy and use the forwarding hierarchy address, or port number, to work in order to work in this hierarchy. For example, http is equivalent to using port 88.
The protocols that work in the application hierarchy are:
HTTP (Hyper-Text Transfer Protocol) : TCP-based protocol using port number 80.
Telnet : Use TCP port number 23. Use this protocol to connect remote terminals
SSH (Secure Shell) : Services like Telnet are vulnerable to security. Because the password is unencrypted, it is displayed as is. SSH is a complement to this. Use port number 22. A protocol such as SFTP is also used primarily on port 22.
FTP (File Transfer Protocol) : A file transfer protocol. FTP is used to download and upload files. FTP works with TCP because reliability is important when uploading or downloading files. Two ports are used.
TCP port 20 is used for data transfer and TCP port 21 is used for control.
Simple Mail Transfer Protocol (SMTP) : Mail transfer protocol. It runs over TCP and the port uses number 25.
POP3 (Post Office Protocol Version 3) : The protocol for receiving mail. Programs such as Outlook work using a protocol called POP3. Use TCP port 110.
Domain Name System (DNS) : Provides host information for a domain name. It basically runs over UDP. Basically, if you fail, you can request it again, and it’s not that important information. However, it also runs over TCP if reliability is required. Long data can operate on a TCP basis at the same time.
Use UDP, TCP port 53.
As you can see, some ports cannot be used if the port number is used by a specific protocol. These ports are called well-known ports.